PSK - WPA2
08. What is the wifi-mobile AP password?
For this challenge we have to obtain the password of a normal PSK network, for this we have to monitor the traffic with “airodump-ng” and wait for a client to connect or force a deauth attack with “aireplay-ng”.
sudo airodump-ng wlan0mon -c 6 -w wifi-mobile
In parallel
aireplay-ng→ Part of the Aircrack-ng suite, used for packet injection.-0→ Specifies a deauthentication attack.10→ Number of deauth packets to send (in this case, 10 packets).-a F0:9F:C2:71:22:12→ BSSID (MAC address of the target AP).wlan0mon→ The wireless interface in monitor mode.

Once we have the handshake I recommend waiting a few minutes capturing with “airodump-ng” to be able to decipher the traffic later using “airdecap-ng”.
If we do this correctly we get the handshake, which can be easily cracked with aircrack-ng.


starwars1
09. What is the IP of the web server in the wifi-mobile network?
If we have a handshake and the network password, we can decrypt the traffic of each of the users after the handshake, making it very similar to the open networks in the previous section.
To decrypt the traffic, you need both the Network Password (PSK) and the specific 4-way Handshake for that individual user.
If you have the password but missed the handshake for a specific device, you will see their traffic as encrypted "noise" that you cannot read
For this we can use “airdecap-ng” and then open the generated file with “Wireshark” to obtain the IP of the HTTP server.


In this step we can save the cookies for a future task.
PHPSESSID=7ulh4rg3tu8gfnbomp0v9s35r3
PHPSESSID=e1is7u87gm0uv509av76mc3p2k
10. what is the flag after login in wifi-mobile?
Get wifi-mobile users traffic passively (802.11), decrypt and login with stolen cookies to wifi-mobile’s AP router to get user FLAG.
The first thing we have to do is to connect to the network, for that we can use “wpa_supplicant” again, with the following configuration file
psk.conf


We can use the session cookie to access with the session and obtain the flag. Change the cookie and go to the servers IP.

Refresh the page and we get the flag.

11. Is there client isolation in the wifi-mobile network?
Get flag from the other user’s web server.
To do this we can use “arp-scan” to get the IPs and curl their HTTP server to get the flag.
arp-scan→ The tool used to scan and list active devices on a network using ARP requests.-I wlan3→ Specifies the network interface to use (in this case,wlan3).-l→ Stands for local network scan, meaning it will scan the entire subnet of the connected network.


flag{edfdf342848f5559bce9750c98b7018da3d9270e}
12. What is the wifi-office password?
The wifi-offices network is not visible, so it is in another location or maybe it is no longer there, but we can still get its password by creating a fake AP with “hostapd-mana” and get the handshake of the clients that ask for this network in their Probes to perform a dictionary attack against it and get the password in clear text.

hostapd.conf

CTRL+C when AP-STA-POSSIBLE-PSK-MISMATCH.
Once we have obtained the handshake we can crack it using “hashcat”
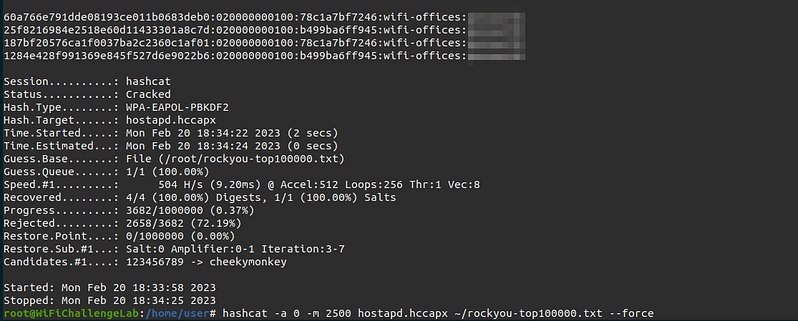
In case the 2500 mode does not work you can convert the hash from 2500 to 22000:
Save the hccapx to pcap

Export the 22000 hash mode from the pcap

Crack outside the VM or with a new version of hashcat.


password1
Alternate Method - Cracking with Aircrack-ng


Last updated